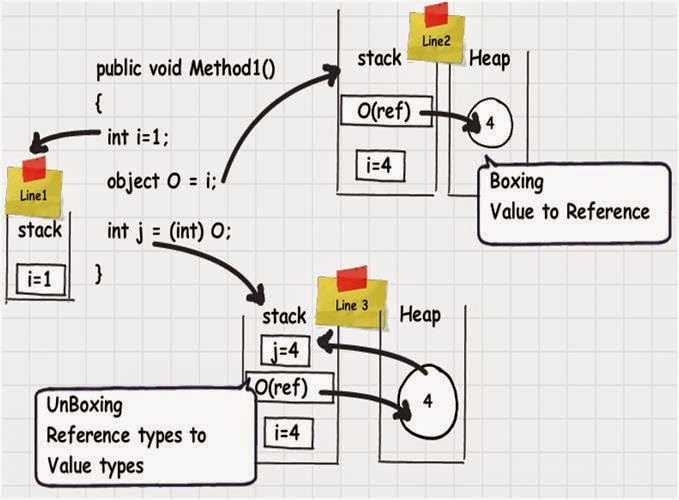
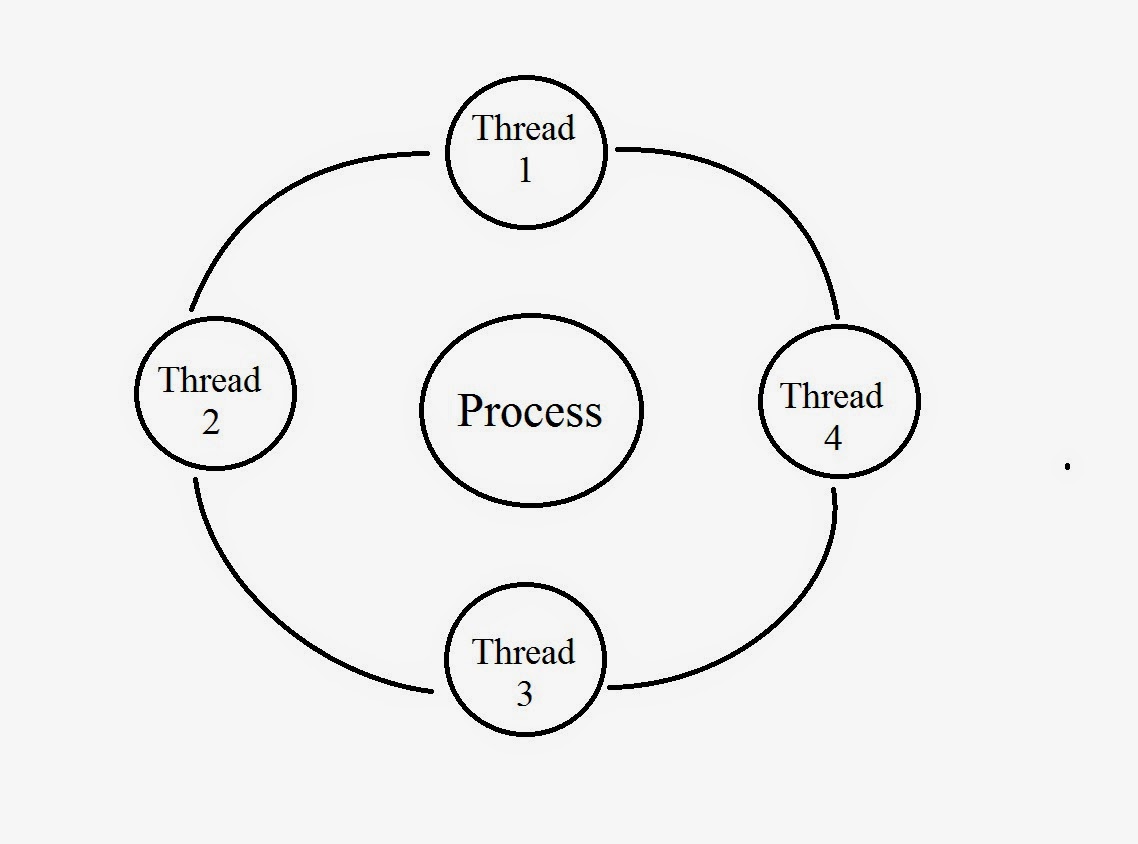
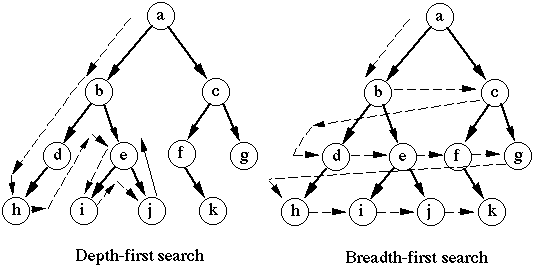
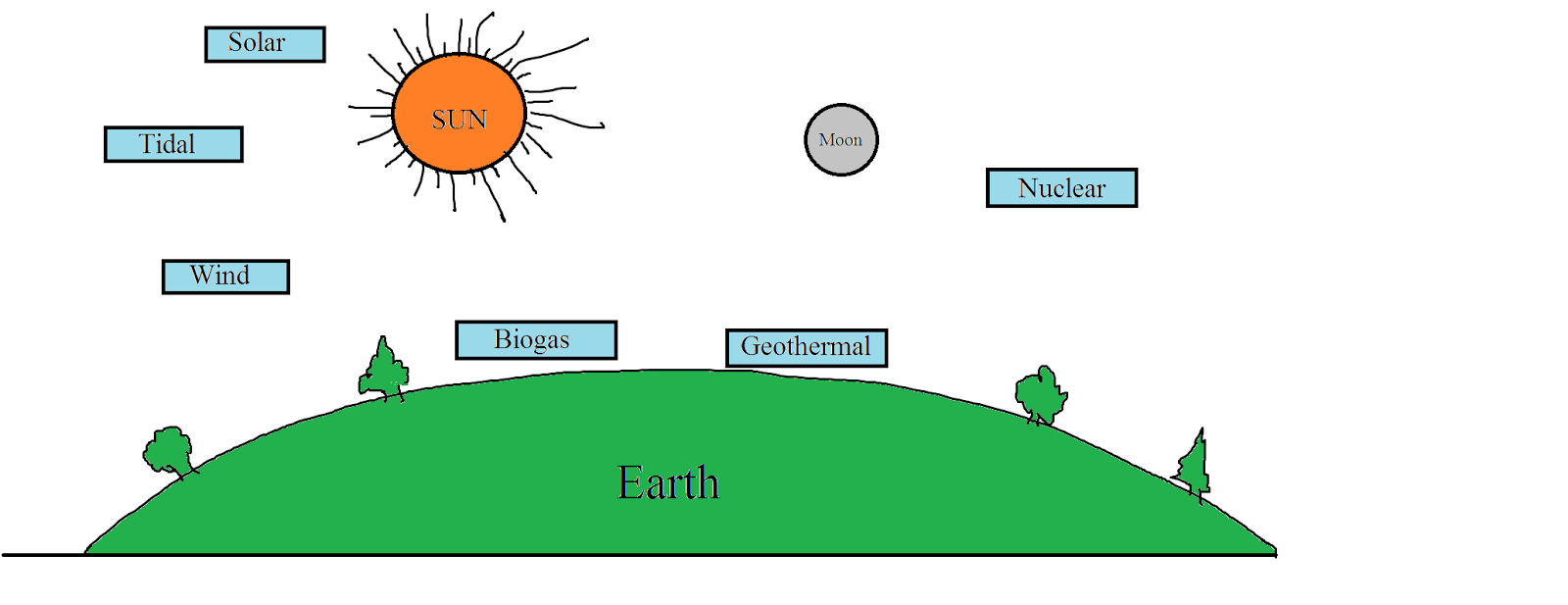
.Net - Important Interview Questions
OOPS Concepts SQL Concepts Web Concepts Windows Concepts Crystal Reports & Sql Reporting Services Why used Crystal reports in applications? Client-Server Concepts Remoting Web Services .Net Framework Application Domain Polymorphism Primary Interop Assemblies (PIA) What are System Exceptions & Application Exceptions? Where and why to use both exceptions?